Key benchmarks from the Ponemon Institute you need to start implementing
Even though 85% of organizations offer cybersecurity training, the well-documented cybersecurity skills gap isn’t going away. It’s only getting worse. Meanwhile, a striking 59% of cybersecurity professionals report that their organizations could be doing more to address the skills gap, while one-third note that their organizations could do much more.
So, what gives? Companies do not have adequate cybersecurity training programs.
The Ponemon Institute study on Cybersecurity Training Benchmarks has explored what the best practices for successful programs are. Not only were the answers clear, but there was a direct correlation between an organization’s security posture as measured by the well-documented Security Effectiveness Score (SES) and their adoption of these training best practices.
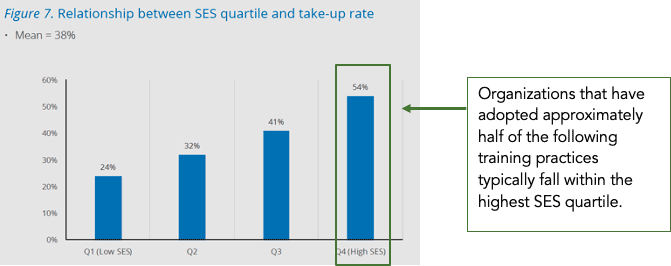
The quality of the content in a training program is an obvious factor. However, how a program is measured, delivered, and governed are equally critical factors to success - or failure. As Ponemon groups best practices into three primary areas and 17 specific activities, that’s how we’ll explore them here and look at ways to implement them within your organization.
Security Effectiveness Score Explained: The Ponemon Institute measures security posture in this benchmark study using a well-defined performance measurement tool called the SES. This tool has been validated in more than 50 independent studies since its creation. The score captures all elements that lead to a strong security posture on a scale from 1 to 10 (worst to best).
How Effective Is the Content In Your Cybersecurity Training Program?
Learning skills can’t be in a purely hypothetical environment. Consider the unrealistic expectation that a child should learn how to hit a baseball by just listening to an explanation of how to swing a bat or by watching a baseball game. Learning by doing, hands-on learning, or experiential learning - whatever you want to call it - enables skill development and mastery.
While theory has an unquestionable place in learning, hands-on experience and practice turn concepts into skills. Simulation as a learning technique shows real-world consequences, creates muscle memory, delivers meaningful cause and effect experiences, and can provide relevant feedback at critical learning moments. It also encourages failure, experimentation, and trial and error.
This is why a multimodal, or blended approach, is critical for any training program. Teaching your team fundamentals and advanced theories in online courses is powerful. But coupling these learnings with simulation generates more than twice the ROI for your training program. It also makes the content feel closer to their day-to-day job and thus more consumable. Consider adding live cyber range hacking events to your program or provide access to realistic, hands-on cyber ranges to test their skills as they go.
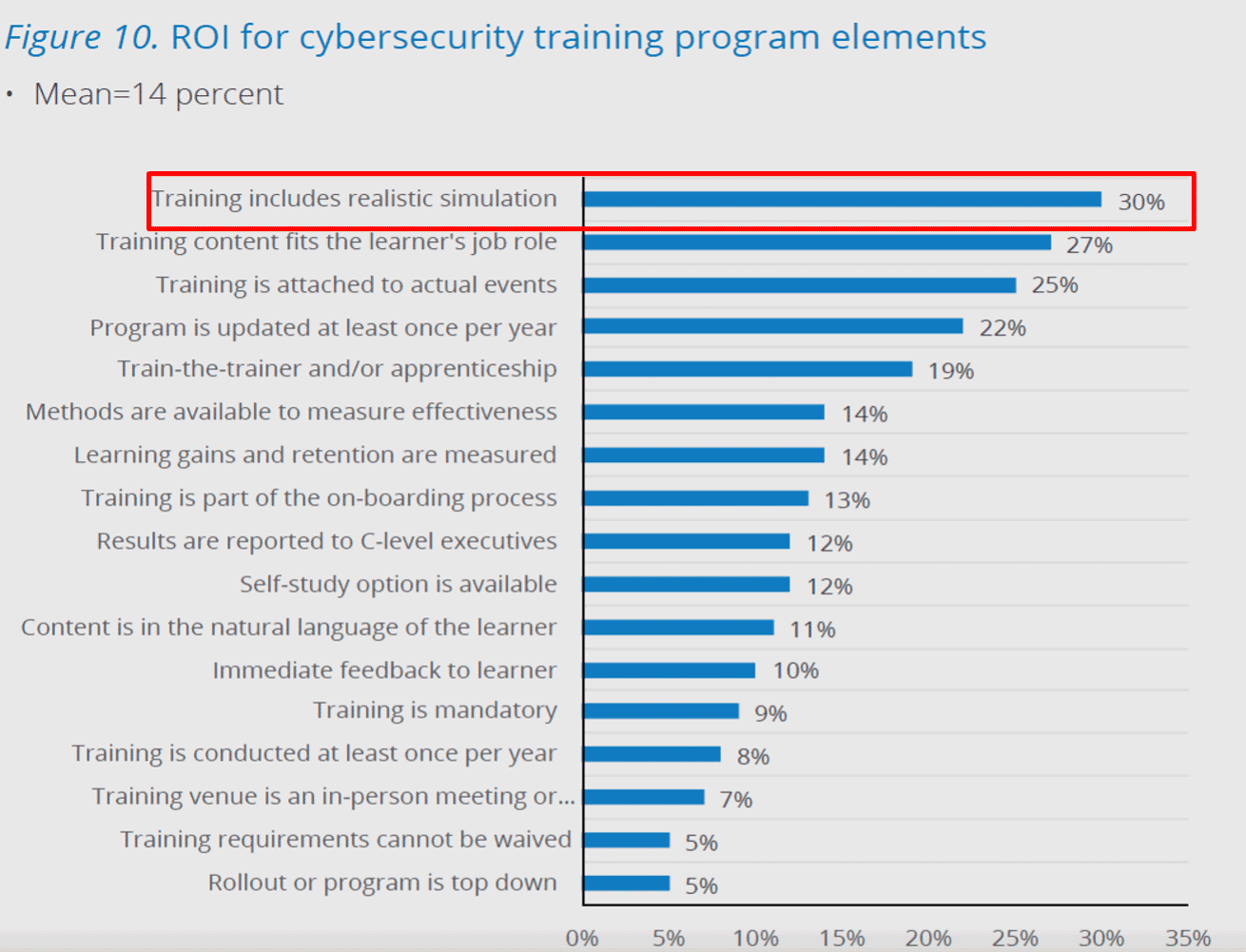
Along the same lines, making the training culturally relevant helps the learner connect with the material. By bridging the training to real-world events versus referencing fictional scenarios, learners better adopt the mindset that those events could happen to their company. This urges them to consider whether they could expose their organization similarly, resulting in important situational awareness.
Cybersecurity training will encompass many teams - from your developers to IT and your InfoSec teams. Learning paths should be specialized by team, role, and proficiency in the key competencies related to that specialty. This best practice is a key differentiator between generic, one-size-fits-all cybersecurity training programs that don’t move the needle and the highly customized training that not only demonstrates skills improvements (more on that later) but is also more engaging.
Job-specific training scenarios allow learners to solve the real problems that they face daily. It can also help to reduce staff turnover (Hello, Great Resignation!). A recent study showed that 70% of participants confirmed “job-related training and development opportunities influenced their decision to stay at their job.”
According to Learning Solutions, a leading industry publication for eLearning professionals: “Over and over, eLearning experts emphasize that in order to be engaging, training has to be relevant to the learners. Offering learners focused training that is directly applicable on the job, and, even better, creating personalized learning paths, will increase learner engagement. They will spend more time on the training, pay closer attention—and potentially improve their performance as a result.”
A final best practice is the option for learners to self-study. On-demand courses give learners the flexibility to learn at their own pace and to circle back to it after other new knowledge. Self-pacing can improve memory performance, particularly when the learner allocates more time to the more difficult material.
To recap, here are the five key benchmarks that are critical to the success of your training program:
- Training includes realistic simulation
- Training content fits the learner’s role
- Training is attached to actual events
- A Self-study option is available
- Content is in the natural language of the learner
Does Your Training Program Have the Right - or Any - Performance Measurements in Place?
You’ll be hard-pressed to find a high-growth, high-achieving organization that isn’t goal-driven and focused on measuring the right performance indicators. Measuring just for measurement’s sake is pointless and a waste of time that no one has any extra of these days. As the person responsible for the cybersecurity training program in your organization, you need to be sure that you are spending your precious time on the right measurements.
First, you need to make sure that there are measurements in place to prove that the training is effective. This is true at both the individual and organizational levels. Then, you should have data demonstrating learning gains and measuring the retention of knowledge. At the learner level, your program should also be able to give immediate feedback on performance.
Baselining skills is essential for both the development of individual learning paths and benchmarking learning gains, as well as for overall program effectiveness. As with learning paths, the more personalized the assessment, the more powerful it is as a business tool.
For example, an assessment that ties to an industry-recognized framework, such as the NICE Framework, has numerous benefits. Individual results can be aligned with roles and measure proficiency. They can be compared to industry benchmarks, set clear career and learning paths, and be a tremendous resource for not only retaining and cultivating top talent but also understanding where there are talent gaps on your teams.
An additional benefit of measuring results is the ability to set competency bars. This allows for training goals for team members and can be used as part of a security champion belt program or other incentive-based initiatives.
One final way that measurements can be beneficial to individual learners is by providing immediate feedback. This cybersecurity training program best practice is proven to increase motivation, perseverance, and knowledge retention. Immediate feedback can be delivered as cause and effect in a simulation exercise, a branched learning scenario, or instant confirmation of a correct/incorrect response, for example.
The three key measurement benchmarks for your training program include:
- Methods available to measure effectiveness
- Learning gains and retention are measured
- Immediate feedback is given to the learner
Does Anyone Care About or Attend Your Cybersecurity Training?
The notion of the importance of “governance and delivery” as a critical component of the success of your training program seems like an instant snooze-fest, but in reality, the Ponemon research identified nine out of the seventeen best practices in this category - and for good reason. If no one cares and no one attends, there is no way that your training program can make a difference to your organization’s security posture, let alone a significant one.
Within program delivery are several best practices that should be part of any training program. Training starts on day one for new employees. Making training a part of the onboarding process starts to engrain it into the culture, at least for the new hires. Participation in the training program also needs to be mandatory - no opting out because they’re too busy or “already know it all” (more about the role of culture later).
You can’t force anyone to absorb knowledge they don’t want to, so try to approach “mandatory” with an inspirational perspective. The automotive industry training is as inspirational as it is educational. It focuses on the safety of life of the people that they are building the cars for. Imagine if this safety training were optional - safety of life then becomes an afterthought. Consider tying your training to your organization’s mission; it’s not mandatory, it’s mission-critical and inspirational by connecting it to the larger why. Technical and security professionals are inherently curious and want to do the right thing – give them a reason to stay that way.
Training programs need to be ongoing and continually updated based on the latest threat intelligence. Technologies, attacks, zero-day exploits, and more - things that keep your CISO up at night - emerge on a daily basis. By making sure that your training is up-to-date, you are not only keeping your team up to speed on the latest threats, but you are empowering them with the skills needed to ensure your product meets the constantly evolving security demands of your clients. This is where the dreaded skills gap can become a critical business risk.
Principles-based training has a much longer shelf life as the content is not technology-specific. However, content should be coupled with hands-on learning to address current threats or technology trends. This ties back to the importance of multimodal training programs and the importance of ongoing training. Conducting multiple, live training sessions per year allows for ongoing practice, skill reinforcement, and a growth mindset, and supports the critical notion that your organization understands learning is a constant evolution, not a single point-in-time effort. Plus, consistent, ongoing training increases knowledge and skills. In one instance, we’ve documented a 37% average score increase among a 10,000+ user group between their first and second live cyber range event.
Live events are also a key best practice for your program. While this used to mean an in-person or classroom-type experience, we’ve seen tremendous results from instructor-led events that have been remotely held since the spring of 2020. Team functionality in cyber range events allows learners from across various departments and roles to see first-hand that they are in this together and can actually have fun as a team. If you’re asking yourself when was the last time they had fun in a training session, that’s a best practice that we believe in, and we’ve seen the impact of time and time again.
Train-the-trainer and apprenticeship programs are best practices reflective of the organizational maturity of your training program. This is often seen in software development teams with the building of a security champions program. As the team progresses through the training over time, they are in a unique place to help scale AppSec knowledge and reduce the dependency on (and sometimes friction with) the security team.
The final area of best practices for your cybersecurity training program is all about culture. It’s critical for adoption that learners understand training is not just a team priority but an organizational priority with visibility at the highest level. Knowing that the program has C-suite visibility and support connotes a level of importance, seriousness, and commitment expected by the organization.
This doesn’t mean doom-and-gloom emails from the C-suite, though. Our client, Accenture, noticed significant spikes in enrollment and consumption when management announced the program and sent occasional encouraging emails to employees on the importance of the training program. We’re all busy and understand it’s a challenge to juggle priorities. Knowing that the folks at the top think it’s a priority certainly helps nudge things up on the to-do list.
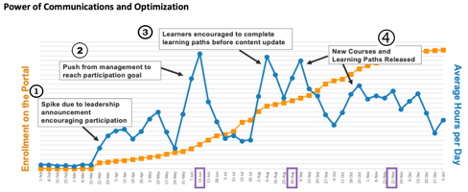
To close, here are the governance and delivery best practices to build into your cybersecurity training program:
- Results are reported to C-level execs
- Training is Mandatory
- Training is part of onboarding process
- The rollout of the program is top-down
- The program is updated at least once a year
- Training requirements can’t be waived
- Training is conducted at least once a year
- Training venue is in-person or classroom
- Train-the-trainer or apprenticeship delivery options are available
Next Steps
It may seem daunting to start your own journey developing a best-in-class training program but fear not. Start by taking our online assessment to see how your current training program stacks up to the benchmarks laid out by the Ponemon Institute. You’ll identify areas for improvement and where your program meets the recommendations. You’ll also receive the full Ponemon Institute Cybersecurity Benchmarks report to help get your team on the path to success.
About Lisa Parcella, Vice President of Product Management and Marketing
With a background in security awareness, product management, marketing communications, and academia, Lisa leverages her vast experience to design and deliver comprehensive security-focused products and educational solutions for the company’s diverse client base. Before joining Security Innovation, Lisa served as Vice President of Educational Services at Safelight Security. She holds a B.A. from the University of Vermont and an M.A. from Boston College. Connect with her on LinkedIn.



