As organizations commit to having security-minded cultures, they are putting a higher focus on Application Security. That means a lot more than writing secure code. According to the 2020 Open Source Security and Risk Analysis (OSSRA) report, open-source software comprises 70% of a modern enterprise application, i.e., code your teams don’t create themselves. The study further reports that 91% of commercial applications contain outdated or abandoned open source components.
The implications are clear – you need to secure the software that runs your business during non-coding activities: procurement, design, development, QA, deployment, and live operation. With a security skills shortage and an explosion of software development, it’s time to get creative to spread security skills and know-how across development teams. Gone are the days when the security team holds all the security knowledge. Especially as organizations are moving toward a continuous integration/continuous development and DevOps environments, every stakeholder needs to be at least security-aware in some respect. Security teams aren’t scalable, so the best way to scale AppSec is to spread the load.
Security Champion programs are a popular way to do this. In a recently released report titled “Building an Enterprise DevSecOps Program,” security analyst Adrian Lane notes:
“I spoke with three midsized firms this week — their development personnel ranged from 800-2000 people, while their security teams ranged from 12 to 25…. Regardless of how you do it (assigning security champions to development teams), this is an excellent way to scale security without scaling headcount, and we recommend you set aside some budget and resources — it returns far more benefits than it costs.”
In the context of software security, a Security Champion is an embedded member of the software development team, not part of InfoSec or Risk Management. They are often an architect or developer with interest in security which they use to improve security practices, amplify the security message, and mentor other team members. This makes conversations about security and functionality tradeoffs smoother because developers are often resistant to adding new tools or activities to their development lifecycle for fear of slowing down production. They have a lot of pressure to get a certain number of features out by a certain time, which is understandable. So hearing about security from one of their own is often received a lot better.
Security champions don’t need to be security pros; they just need to act as the security conscience of the team, keeping their eyes and ears open for potential issues. Once the team is aware of these issues, it can then either fix them or call in security experts to provide guidance. With a security champion, an organization can make up for a lack of security coverage and skills by empowering team members to act as a force multiplier, peer-teach security practices, answer questions, and raise security awareness.
If properly trained and supported, security champions translate application security into a language that the rest of the software engineers understand, yielding the following organizational benefits:
- Scale – Security champions address many of the dev team’s basic security questions and requirements, allowing security teams to focus on the more challenging ones.
- Speed – Security champions are part of the development team. This means they work with the team from day 1 of a project, applying their security expertise to requirements and design decisions early on. They help the team avoid poor security decisions that take time to undo later. Remediating security issues earlier in the process avoids time-consuming “fire drills” that delay release.
- Alignment – Developer security champions help bridge the security-development gap by facilitating discussions and increasing the development team’s credibility.
Implementing Security Champion Programs
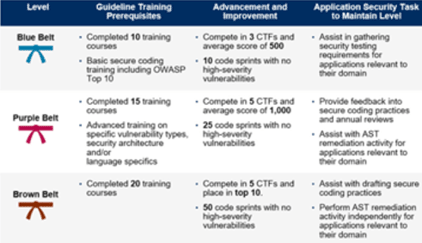 Gartner recommends security champions, though they call them security coaches. A “belt system” of training that combines formal learning with hands-on practice and incentive program significantly increase adoption and success rates. As you can see in the diagram to the right, Gartner recommends formal training, whether it’s computer-based or classroom, and then a learn-by-doing component, like a cyber range or other simulation activities. Applying the new skills with some specific job activities cements the skill into mastery, which makes it easier to teach to someone else.
Gartner recommends security champions, though they call them security coaches. A “belt system” of training that combines formal learning with hands-on practice and incentive program significantly increase adoption and success rates. As you can see in the diagram to the right, Gartner recommends formal training, whether it’s computer-based or classroom, and then a learn-by-doing component, like a cyber range or other simulation activities. Applying the new skills with some specific job activities cements the skill into mastery, which makes it easier to teach to someone else.
Implement a program for recognizing training milestones and skills development…. designate a “belt” system to indicate the level of expertise and recognize progress 3 Steps to Integrate Security Into DevOps
To be successful, security champions need the support of a formalized, management-backed program with ample time for learning and knowledge/skills transfer. It’s also critical that organizations create an engaging, motivating environment where application security champions want (even look forward to) the training sessions.
Security Innovation Security Champions Program
Traditional training methods can be limited, focusing on a singular part of the software ecosystem, e.g., secure coding. It is proven that programs that don’t include realistic simulation and role-based content are less effective.* Integrating those two qualities within a progressive belt system makes for the most effective training program possible.
The program we offer at Security Innovation combines self-paced computer-based training, hands-on cyber range challenges, and mentorship activities designed to facilitate progression through a series of “belts” or “levels” of maturity.
This goal-oriented approach increases adoption rates and creates permanent behavior change through:
- Rewards & Recognition – Motivate participation to learn more and strive for the next belt.
- Engagement – Solidify concepts and apply new skills via hands-on activities.
- Measurement – Ensure employees are on track and goals are met to justify the investment.
Because each customer is different, we have pre-defined role-based learning paths tailored to specific job activities. Our application security training program incorporates hands-on labs using intentionally vulnerable applications, interactive computer-based training, short instructor-led training sessions, and a variety of “learn on your own” activities. We also offer an optional SDLC security assessment to identify gaps for other roles and phases of the application lifecycle.
Our learning management system automates the belt program for each user, making it simple to track progress, milestones, and metrics for organizations of any size. At each tier, there is an element of formal training as well as hands-on exercises.
For a more experiential approach, activities can be paired up with appropriate belt levels. For example, users are asked to complete tasks that correlate with the training topics they’re learning about, such as:
- Participate in a security issue analysis
- Conduct a security code review
- Learn a new security tool or process
- Design or develop a security feature
- Lead a security test
- Conduct an SDLC risk review
Pre- and post-assessments are also used to measure knowledge and retention over time, whilst “lunch and learn” sessions can be leveraged to address timely industry issues, emerging threats, or internal challenges. Remember that as employees progress, it’s important they’re recognized and rewarded for their efforts. Belts can be tied into job performance, salary reviews, and utilize badges or other publicly visible recognition elements.
Essential Elements to Our Belt System:
- Micro-module approach – our short, topic-based courses allow teams to mix and match based on job function and needed security competency
- Assessment & Measurement vehicles –full-featured and live applications, our cyber range presents challenges for learners to tackle while we measure their progress in real-time. This is a keenly accurate way to assess security acumen on deployed applications. They quickly identify rock stars, often to the surprise of our clients.
- Progressive training – our courses and cyber ranges have various difficulty levels to ensure sequential learning
We apply those 3 critical elements referenced in Gartner and Ponemon Institute research: role-based training that includes realistic simulation and a combination of formal training with hands-on practice activities. We further make sure that your program meets expectations throughout its life span:
- Before: help you set specific, measurable, attainable, and realistic/time-based objectives
- During: optional monthly or quarterly business reviews to track progress and ensure participants are fully focused on achieving the set learning objectives
- After: ensure knowledge is brought back to the development teams to help them design, build, test, and deploy applications that are more secure
Security Champion and Belt Programs in Action
Accenture
Accenture set a goal of training nearly 80,000 developers to identify:
- Security Champions for development teams
- Candidates to move to AppSec team
This was ideal for constructing a Belt Program. We created 24 role-based learning paths based on 3 progressive skill levels. Computer-based Training (CBT) scaled knowledge quickly, and our cyber range provided a safe sandbox to practice and master new skills. Accenture set “scoring bars” for Security Champions and AppSec team candidates based on real-time performance on the cyber range.
After 12 months, over 110,000 developers were trained, a Belt Program with measurable competency gates was fully functional, and dozens of developers had moved to the AppSec team (with higher bill rates), saving hundreds of thousands of dollars in recruiting fees.
Learn more about Accenture.
Orvis
Previous training wasn’t generating the desired excitement or engagement that leadership desired. They decided to take a fresh approach with hands-on cyber ranges. Not only was it met with excitement where teams no longer dreading training, but it was the genesis for their AppSec apprenticeship program. While this was not planned, Security Champions emerged organically. Several developers continued their pursuit of security principles beyond the events, so much so that they were able to lead future events and provide on-the-job mentorship to junior developers.
Learn more about Orvis.
Illumio
Illumio sought to bring security and exploit capabilities to their development teams. Leveraging our live-action, authentic environment cyber ranges, Illumio was able to assess team and individual strengths that revealed valuable opportunities for mentoring (aka “security champions”). Those that demonstrated competency assumed broader security responsibilities on the team and continued their training with more advanced courses and cyber range exercises.
Learn more about Illumio.
*Cybersecurity Training Benchmark Report – The Ponemon Institute, 2020
About Lisa Parcella, Vice President of Product Management
With a background in security awareness, product management, marketing communications, and academia, Lisa leverages her vast experience to design and deliver comprehensive security-focused products and educational solutions for the company’s diverse client base. Before joining Security Innovation, Lisa served as Vice President of Educational Services at Safelight Security. She holds a B.A. from the University of Vermont and an M.A. from Boston College. Connect with her on LinkedIn.


