The 2022 Spokane Mayor's Cup CTF
Cold, Pacific Northwest rain battered against the windows of two packed cars as they drove the winding highway through Snoqualmie Pass. We were headed from Seattle to Spokane, two vehicles full of hackers and developers, all giving up a weekend to help coach high-school and college students through a cybersecurity competition that was started a few years ago by one of Security Innovation's very own: Maxwell Dulin.
The 3rd annual Spokane Mayor's Cup Capture The Flag (CTF) Cybersecurity Competition had a pretty simple goal: expose the world of cybersecurity to as many interested inland Northwest students as possible. While some CTF competitions emphasize a highly competitive atmosphere designed to push hackers to their caffeine bolstered limits, the Spokane Mayor's Cup focuses instead on fostering a friendly, welcoming environment where students of any skill level can feel free to ask any questions, learn different technologies, and reach the "aha!" moment that every hacker lives for. All questions, ranging from "how do I run a compiled binary?" to "how do I figure out the amount of columns necessary for this SQL Union injection to work?" are welcome and, in fact, encouraged.
To help students answer these questions, a team of volunteer coaches from Security Innovation and a handful of other software development and security engineering companies went together. We found ourselves excitedly trudging through the rain, packed in a couple of cars, handheld radios and the requisite snacks divided between the vehicles, making the 4 and 1/2 hour trip from Downtown Seattle to Spokane, all to wander through Eastern Washington University classrooms, helping out however we can, brought together by shared passion for cybersecurity.
 Maxwell Dulin provides opening instructions to the gathered students and incentivizes them to win our totally custom trophy.
Maxwell Dulin provides opening instructions to the gathered students and incentivizes them to win our totally custom trophy.
Fog covered not just sections of the road but all the beautiful mountain vistas we were anticipating seeing on this trip through the pass. It didn't much bother us, though. We had a motivation besides sightseeing. It was the same motivation that propelled us through the first half of the CTF where, for the sake of social distancing, different teams of students spread out amongst a number of different classrooms. When the servers spun up at 9 am, each team connected and started hacking on whatever challenges piqued their interests.
Each challenge required students to learn some new technique relevant to the world of security in order to retrieve the flag: a unique string of characters which students then submit on the CTF scoreboard to earn points for their team. Maxwell Dulin has been creating challenges for the CTF over the last three years. The more difficult low-level binary hacking challenges and a good chunk of the web-based challenges were created by him. However, a number of other people also helped create challenges for the event. Ken Price, who also helped coach throughout the day, contributed a series of increasingly difficult cross-site scripting challenges, each one requiring the students to find a different injection technique in order to get their payloads to fire. Fabian Vilela, also another coach, created some OSINT (open-source intelligence) challenges that required competitors to look at static images with no other information and identify either where the photo was taken or who was in the picture. Gerard Johansen contributed a set of challenges that involved combing through Windows event logs to find evidence of intrusions. This same series also involved reverse engineering real-world PowerShell malware droppers.
For about three hours, Florin Stanciu, Nick Huber, Trent Clostio, Vanessa and Maxwell Dulin, Andrew Antles, Joseph Riddle, Ken, Fabian, Gerard, and I helped two-to-five-person teams use Ghidra for the first time, debug XSS payloads, and bypass the unanticipated web application firewall on the University's local network.
After the first chunk of hacking time, the engineers from Security Innovation hosted a Q&A session. The 60+ students, ever curious about the 'real world' of security engineering, listened extremely attentively the entire lunch hour as each of the coaches discussed our road into the field. The goal of the session —and the hope of the coaches and organizers— was that by hearing our stories, the students would find something to draw on that would one day be a part of their stories about finding a path into security. The roadmaps all looked different for each of the coaches. Some didn't start hacking until their 30s and pivoted into cybersecurity from other domains. Some started programming at 10. Some had degrees in computer science. Some had degrees in fields like economics but decided to pivot afterward into cybersecurity. Others even dropped out of college halfway through to hack full time.
Despite these differences, there was one common thread that tied together all the stories and answers about resumes and career planning that the students threw at us. It is the same thread that made us unfazed by the inclement weather, that made us happy to sit with one student for an hour until they grasped a concept. It's the same thread that pushed each of us in different ways to pursue this career field. The same thread that motivated the organizers to begin the event three years ago.
Call that thread passion. Or pure curiosity. Regardless of the title, a working definition might be something like: 'to be motivated to action by the thing you love in and for itself, not just by what it could (or will) bring you.' Many of the best hackers I know and work with are not motivated purely by the money or the accolades that their exploits bring them. The curiosity, the passion to know what this or that input will do to the state of the program or the radio protocol, is the primary driving force behind their work. To put it a different way, as Dulin did with the students before and during the event:
"Curiosity didn't kill the cat. It made the cat great."
Seeing students' faces light up when their newly discovered XSS injection method finally fires that alert(1), or when their custom MD5 hash brute forcing script spits out the correct key, both events growing even more the student's curiosity, is priceless. It propelled the coaching team to not blatantly provide solutions but only give the perfect nudges that allow the student to solve the problem as a result of their own repeated effort and attempts. Each crumb of information being given with the hope it might serve some small part in igniting within each student the fire of the very curiosity that got us all careers in the field. The same curiosity that made the cat great.
 Andrew Antles assists D-Squad, the top scoring team of the lower division.
Andrew Antles assists D-Squad, the top scoring team of the lower division.
This hacker spirit of passionate curiosity revealed itself in a number of fantastic ways over the course of the competition. Some of the students went above and beyond just finding and submitting flags, displaying perfectly the aforementioned hacker ethos. One student, while attempting to exploit a bug in floating-point number calculation, discovered that simply inserting the input "NaN" would cause the backend logic to be totally bypassed, giving him access to the flag. The developer of the challenge did not even know this was a possible exploit. How did that student discover this bug? By following one of the golden hacker rules and pouring over the man-pages of the underlying library calls being made in the source code.
Another moment showcasing that curiosity involved students realizing they could insert new blog posts into the SQL injection challenge page. Blog posts which, of course, have stored cross-site scripting payloads. While having to click through 100,000 Firefox alert boxes that said "collin is cool" proved annoying, and figuring out how to prevent them popping up even more so, I don't think anyone minded too much. The student's realization that the attack was possible and that writing a script to automate it was also possible showed so much of the hacker spirit that we were more than happy to click through and manually clean up the page.
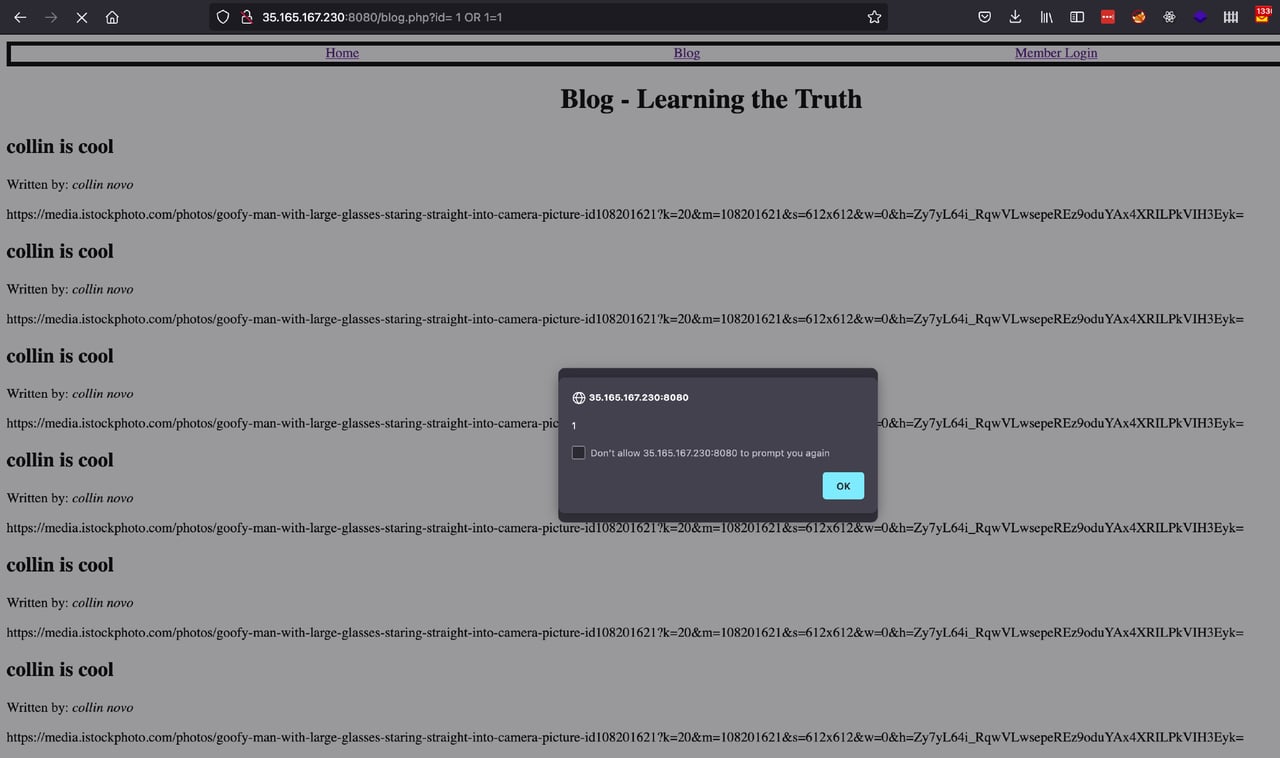 Firefox alert boxes that said "collin is cool.”
Firefox alert boxes that said "collin is cool.”
The after-show discussions generally revolved around each member of the coaching team sharing what our favorite part of the day was. Once again, that commonality in us all showed itself. Each of us loved the students' displays of spirit, and even just talking about (or retrospectively writing about) them caused us all to smile, get excited, and laugh. Discussing the day with the coaching team around pizza and drinks hanging out in Spokane only served to make more evident our mutual passion for our craft and for teaching said craft.
It truly is priceless to see the same spirit that gripped each of us through a book, or a blog post, or a first disassembly dump of a C binary, grip the next generation of hackers. Having the opportunity to play even some small part in that process is a brilliant thing. Passion should motivate both the hacking itself and the desire to see others accomplish fantastic exploits on their own. Getting excited over helping the wider hacking community has forever been a staple of hacker culture. Every hacker ought to give it a try. Maybe even at the 2023 Spokane Mayor's Cup.
 Florin Stanciu, Security Innovation, gives helpful career advice to hopeful hackers.
Florin Stanciu, Security Innovation, gives helpful career advice to hopeful hackers.
One of my favorite moments of the day actually involved one of the 'low hanging fruit' challenges. These challenges are supposed to be simple, quick ways to get on the scoreboard. The answer to the question was a classic reference to longtime hacker culture and a generally requisite part of every CTF challenge set. The student was perplexed why a question with such a low point value was troubling him so much and asked for help. He told me,
"It's so easy, I tried googling everything.... 'Hack the ____,' 'Hack the ____ CTF,' 'hacker hack the quote,' but I can't figure it out!"
I chuckled a bit and thought for a moment. What's a particular hint that would put him on the right track? Two words came to mind. I smiled and told him, 'Angelina Jolie.' He added that to his search queries. Excited and smiling, he quickly found the right answer for the flag.
The famous quote from Hackers that the delighted student said after getting his 50 points (and that other members of the coaching team told many students throughout the day) is what I now end with. Passionately give back to the community, help others learn as much as possible, and of course:
"hack the planet!"
If that ethos motivates you, we at Security Innovation are always wondering, canyouhack.us?
About Nathaniel Kirkland, Security Engineer
Nathan Kirkland is a security engineer at Security Innovation. He specializes in testing web applications, unique cryptographic protocols, and cloud environments. Self taught and brought up on a steady diet of video game modding and borrowed security books, he has a passion for curiosity. Legend says he still keeps his coffee (and tear) stained 1980s edition of The C Programming Language by K&R stored in a box somewhere. When he’s not doing CTFs or working on cryptography projects, he’s probably either enjoying the great outdoors or is in a coffee shop with his head stuffed in a Kierkegaard book.


