Working with rapidly growing products like our CMD+CTRL Cyber Range is fun for a variety of reasons, particularly because seeing people smile while learning is a rare occurrence. For much of the Security Innovation team though, the best experience is growing a technology from an interesting idea to a rapidly maturing product. Even better, the journey allows for many “Aha!” moments in the form of feedback and ideas from our customers.
___________________________________________________________________________
Learn more about Cyber Ranges in our webinar
Cyber Ranges: A New Approach to Security
___________________________________________________________________________
Luckily for our team, the Cyber Range has an additional audience many products don’t in the form of Capture The Flag (CTF) competitions at numerous OWASP, ISSA, regional and corporate meetings and shows. The growing demand for AppSec skills has enabled our team to run multiple Cyber Ranges each week for new learners and old hats alike. These events are a treasure trove of ideas and recommendations, but also provide our team the opportunity to observe trends and techniques that may otherwise be missed.
One of these trends is the usage of tools in security testing, which naturally need to be balanced with human abilities for optimal impact. Unfortunately, Cyber Range events are enabling our team to observe a common occurrence among security professionals - a small, but notable number of practitioners who are highly skilled with tools, but struggle when those tools hit their limits. To put it another way, there are a lot of well-trained security professionals who need to expand their skill sets beyond the comfort of their tool boxes!
As with most trends, this was discovered after a bit of head scratching. Our team routinely preaches the benefits of a minimal tool approach to enable initial learning, but frequently see a handful of quickly rising scorers at the beginning of an event, who then seem to hit a ceiling for the remainder of the day. After a few months of digging around, it became clear that this was the result of skilled tool users who had limited manual skills. While we don’t discourage using tools, we do want participants to learn, and the reliance on tools was clearly getting in the way of that.
In addition to this trend, numerous questions about the number and quality of tool findings in our Cyber Range have been entertained, so we decided to unleash a handful of tools on Shadow Bank, our most widely used Cyber Range, to see what they found. The tools used included OWASP ZAP, Vega Scanner and SQLMap, as well as several commercial scanners. All were run initially with limited configuration and had several additional passes made with better tuning. In order to avoid a tool bake-off debate, we’ve combined the results below. Out of 120 unique pages/URLs visited, the tools found:

These results are mirrored at events where even the best tool-focused users have found fewer than a dozen issues with deep tuning and exploration - that’s less than a quarter of the vulnerabilities built into Shadow Bank! Ultimately our sites simulate real-world environments where multi-faceted attacks are required to exploit most issues - the exact types of attacks scanners have difficulty identifying.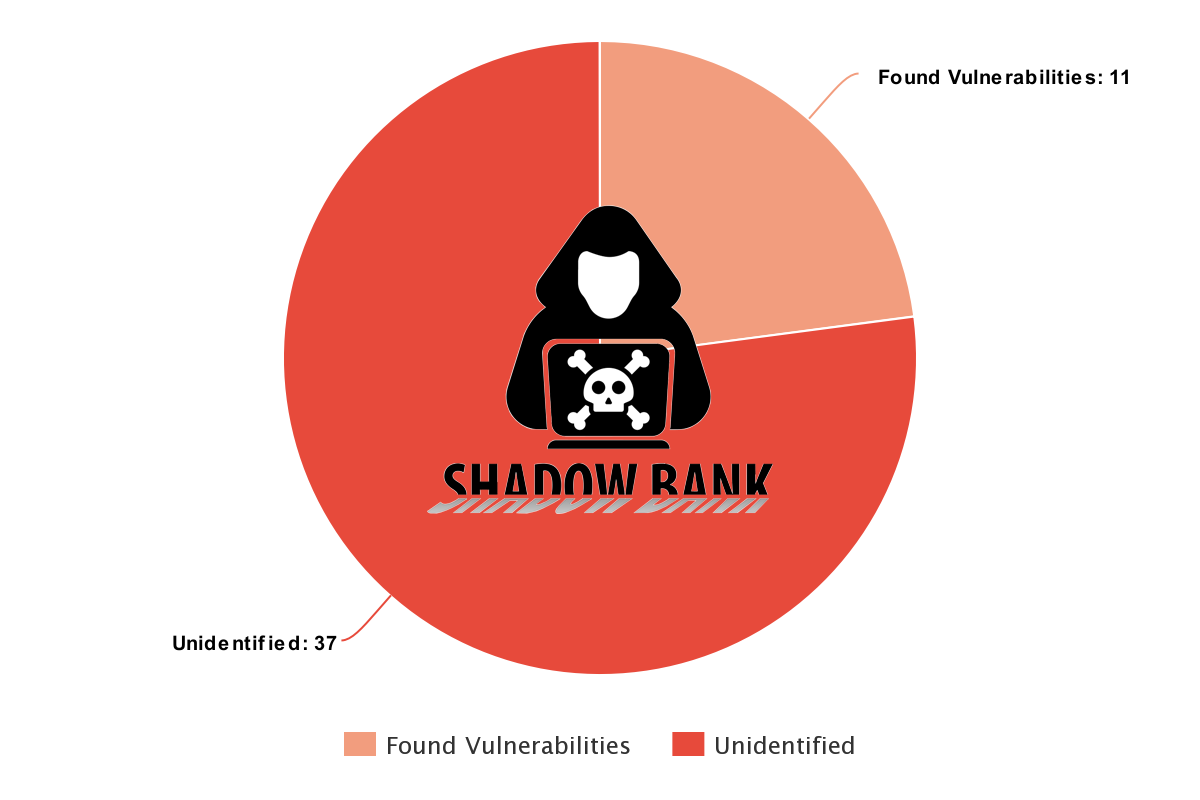
As one might imagine, our product and engineering teams are very happy with these results. They originally set out to develop intentionally vulnerable websites that teach individuals to think like an attacker while minimizing an over-reliance on tools. As our Cyber Ranges have grown, our team has continued focusing on human training and have had considerable success in doing so.
Of course, every tester and every tool is different, so we want to hear more from our Cyber Range users! If you’ve had great success with tools in our Cyber Range, let us know! If you think you can improve on the above observations, attend one of our upcoming events or reach out to our team to schedule one!
___________________________________________________________________________
Learn more about Cyber Ranges in our webinar
Cyber Ranges: A New Approach to Security



