To remain current with technology and threat trends, we update our training every quarter. While we enjoy showing off our new content, it’s just as important for our customers to understand why we separate and conjoin and how learners consume certain topics. Customer feedback, internal SME reviews, and research on industry and technology trends also help shape our content roadmap.
Our Q1 update entails a lot of new and updated content aimed at helping developers prevent certain vulnerabilities and protect data in a variety of development languages and platforms.
- Enhanced coding interactions make it easier to distill complex topics and commit knowledge to memory
- Language-specific vulnerabilities and platform-specific hardening techniques ensure learners have the EXACT knowledge to mitigate vulnerabilities and prevent common attacks
- Tighter Alignment to the NICE Cyber Security Workforce framework to facilitate the mapping of courses to specific knowledge, skills, and abilities (KSAs) required to perform security tasks
- Deprecation/Realignment of courses due to outdated techniques or the separation of topics into microlearning modules for highly contextual on-demand learning
New Courses:
|
Updated Courses
|
Keeping Developers in the Know!
This quarter’s new and updated courses include advanced coding interactions with prevention strategies and data protection methods for the respective programming language. These are delivered via character-driven scenarios that make the concepts more relatable to developers.
Example: Java Security
We added content on hardening the Java application server due to our research about how many Java applications & servers are compromised. We also added scenarios from which developers can learn what leads to race conditions as potentially serious vulnerability. Other additions include detailed explanations and code examples of concurrency issues, shared resource problems, thread-safe code, randomizing temp files, and changed ACL permissions in cross-platform environments. We also expanded training on information disclosure and avoiding hard-coded secrets by adding content around inspecting classes, disassembling JAVA, decompiling JAVA, Error Messages, and Exception Handling.
Example: Integer Overflows
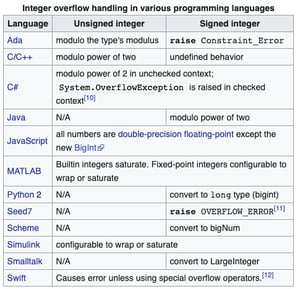 Specific problems become disparate and require specialized knowledge when considered in different development languages. Such is the case with Integer Overflows (IOs) that have become prolific and warrant focus.
Specific problems become disparate and require specialized knowledge when considered in different development languages. Such is the case with Integer Overflows (IOs) that have become prolific and warrant focus.
If you don’t understand Integer Overflows, just think of an odometer on an old car odometer. It’s made of six wheels numbered 0 to 9 and can count up to 99,999.9 miles. The next 1/10th of a mile doesn’t result in 100,000.0 because there are only six possible digits, so the odometer “rolls over” and resets to 0. This gives the misconception that the car has a brand new engine instead of one that has been driven 100,000 miles. Overflow conditions in software often lead to unintended behavior, too.
IOs are more prevalent in Java, Swift, and C derivatives, so developers need to be particularly aware when coding or using software coded in those languages. While secure coding principles are a necessary precursor, getting the right platform- and language-specific guidance is essential as each has unique threats, functions, built-in controls, and syntax.
 The same is true for buffer overflows, cross-site scripting (XSS), SQL injection, and others we address in language-specific modules. There are many different attack vectors, input types, server variables, and mitigation strategies for each. Mitigating SQL Injection is addressed in each of our eight new courses.
The same is true for buffer overflows, cross-site scripting (XSS), SQL injection, and others we address in language-specific modules. There are many different attack vectors, input types, server variables, and mitigation strategies for each. Mitigating SQL Injection is addressed in each of our eight new courses.
Improved Coding Interactivity
It’s essential to make a distinction between improved interactivity and simply more interactivity. Adult learning is a science, and too much interactivity can actually take away from learning efficacy. The objective is to distill complex topics into hands-on learning lessons that convert short-term knowledge into a lasting skill (and long-term memory.) To do this properly without compromising the technical integrity of the lesson takes discipline in applying instructional design.
New interactive coding examples challenge learners to apply knowledge in identifying vulnerabilities within code and demonstrate they can fix them. New lessons now include the ability to "input code" in character-driven scenarios, aligning learning and doing. We designed this code interactivity for learners to experience the results and consequences of their choices in a safe environment. Unlike other solutions that focus on remedial “line of code” hunting, task repetition, or simple knowledge presentation, we solidify contextual relationships through the use of different interactivity types.
Tighter Alignment with NICE Cyber Security Framework
The emerging NICE Cyber Security Framework provides a standard definition of cybersecurity, a comprehensive list of cybersecurity tasks, and the knowledge, skills, and abilities required to perform those tasks. Organizations increasingly rely upon it for workforce development through improved job function classification and skills development. All of our courses are now mapped to specific NICE roles, as well as a primary, secondary, and tertiary roles and target audiences – making it easy to roll out learning paths. Additionally, thecourses are also mapped to NICE Competency Framework Controls, which ensures they are designed to align with objectives to specific knowledge, skills, and abilities.

Planned for 2021
We are continually evaluating how to improve our content, map it to industry standards, and uncover new ways to reach learners. Here’s a sneak peek of what’s coming in 2021:
Learning Labs
A mix of story-based simulations, hands-on exercises, and mitigation lessons, Learning Labs help learners apply technical and operational competencies to identify & remediate errors correctly.
Challenge-Based Learning
Virtual scenario-based interactions that replicate real-life experiences
Skills Assessment
An online tool designed to provide personalized training recommendations, competency insight, improved tracking, and professional journey mapping
Digital Badges/Certificates
Created to be shareable and exportable, they recognize the learner’s achievements and continually motivate them to progress through learning paths
Continued Course Development
Course additions will reflect software’s continuing expansion into IT and Network domains such as MITRE ATT&CK Framework, Network-as-Code, IoT, and cyber exploitation & defense
Want more detail? Check out our course updates in-depth.


