There’s no question that cloud services can accelerate business with instant computing power, on-demand scalability, ease of access, and built-in security controls. However, these features are also attractive to hackers. According to McAfee Cloud Adoption and Risk Report 2019, the average enterprise organization experiences 31.3 actual cloud-related security threats each month, a 27.7% increase over the same period last year.
Despite wide adoption of cloud services and a hostile ecosystem, organizations remain unprepared for the velocity of cloud usage and its expanding threatscape. In fact, over 9 out of 10 companies who participated in Oracle and KPMG 2020 Technology Spending Intentions study admitted that their organization has a moderate (48%) to wide (44%) gap between current and planned cloud usage and the maturity of their cloud security program.To help organizations better address the emerging needs in cloud security, Security Innovation has launched Forescient, a cloud-specific cyber range to its portfolio of insecure environments. Forescient expands into the full stack of business-critical components, including customer-facing front end applications, insecure databases, servers, and cloud services. This new range departs from our existing web and mobile-focused CyberRange suite.
Forescient pushes the boundaries in new ways, including:
- Multiple cloud service misconfiguration vulnerabilities
- Broad internet-wide OSINT clues and challenges
- Common server-side OpSec issues
- All challenges map to the widely adopted MITRE ATT&CK Framework
- Players follow a brand new, innovative, conversational, mission-based playing experience
Cloud subscriber-side vulnerabilities
It is generally accepted that the controls implemented by cloud service providers are more advanced than most on-premises environments. This is primarily because they consider all potential physical threats when building their data centers, including designing, installing, and testing top-of-class physical controls to counteract risks. While the cloud service provider (CSP) is responsible for managing the cloud platform’s security, cloud subscribers are ultimately responsible for securing what is in the cloud. This is not an easy task, and the plethora of data breaches are due to cloud misconfiguration supports that.
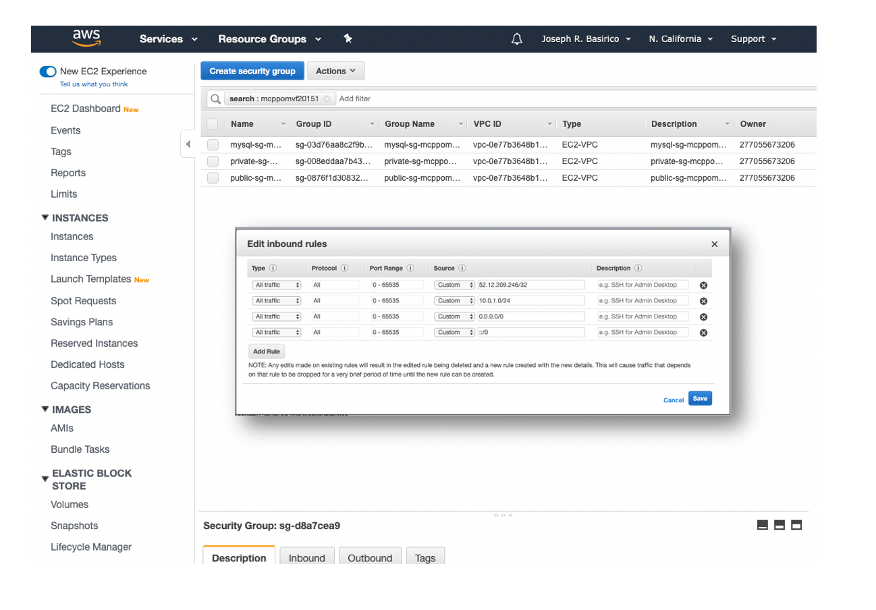
We designed Forescient challenges to reflect the most common mistakes cloud subscribers make, which span the most common AWS services, including EC2, RDS, S3, and VPC. These challenges are heavily focused on cloud misconfiguration, access control, and sensitive data exposure. Configuration management in the cloud has proven to be a significant challenge that has often led to data loss incidents. In fact, Gartner predicts “through 2025, 99% of cloud security failures will be the customer’s fault”.
With Forescient, players become immersed in a real AWS Management Console, a safe sandbox with pre-defined account permission, to experience how configuration rules may strengthen or expose their security posture.
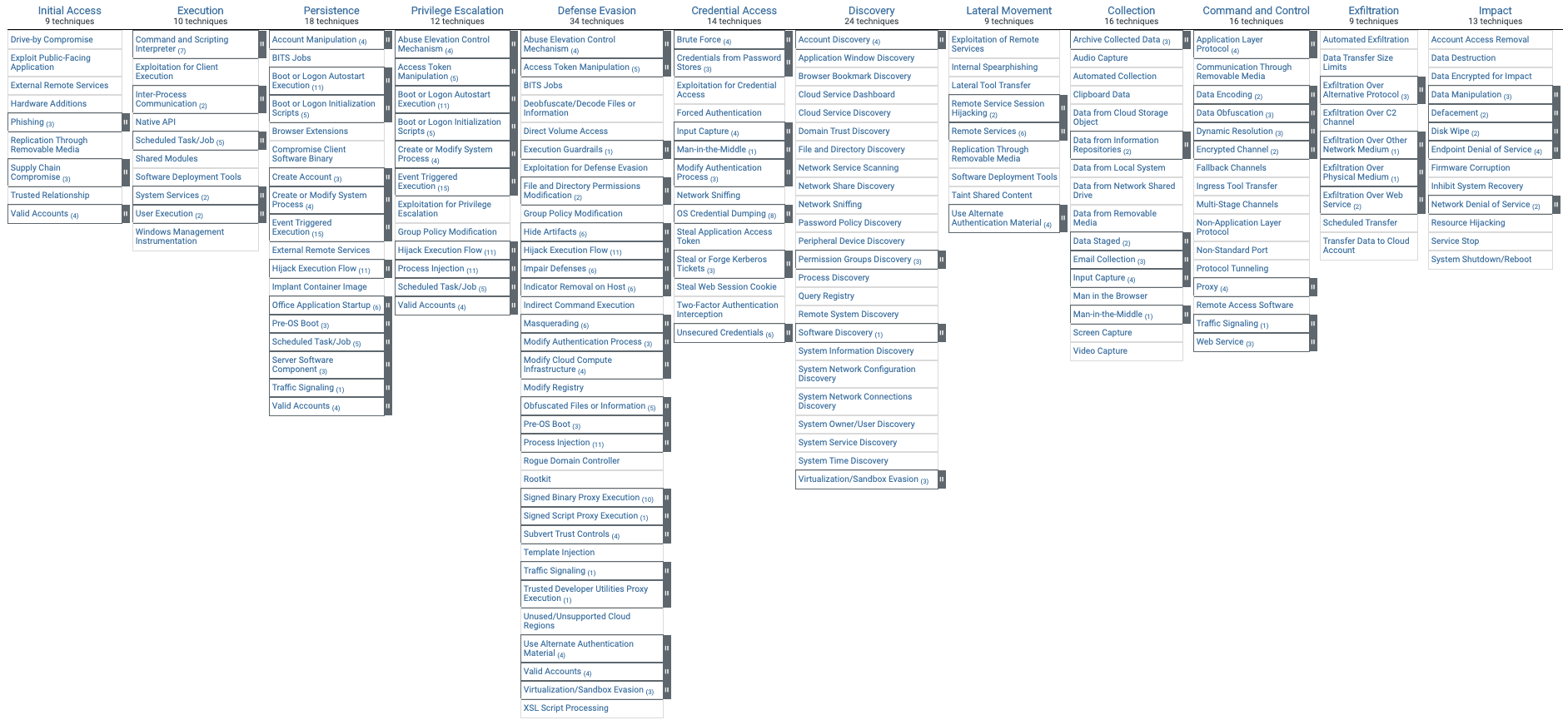
MITRE ATT&CK framework
Because the CMD+CTRL Cyber Range is an authentic framework, MITRE ATT&CK techniques can be used to attack and defend it. All Forescient challenges are linked with the ATT&CK framework so players can refer back to it and discover new avenues of attack. The objective is to help organizations better understand how hackers view cloud systems and their techniques used to penetrate them.
The following ATT&CK techniques can be employed directly in Forescient:
- Account Discovery
- Credentials in Files
- Spearphishing
- Account Manipulation
- Credential Dumping
- Remote File Copy
- Exfiltration
- Data Destruction
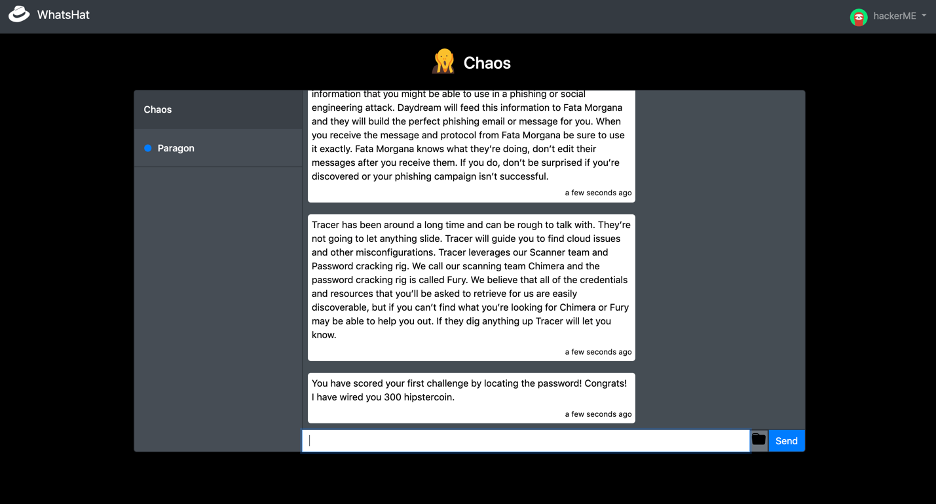
Mission-based playing experience
Forescient features a new and innovative engagement model via an intelligent chatbot. Hackers with diverse personalities are trigged through the chatbot at different times to form a series of coherent storylines. They give specific missions throughout gameplay, so players always know what to do and what to look for. Some challenges are dependent on each other; some are not. This multi-modal approach gives players maximum flexibility to toggle between challenges rather than getting stuck on a single challenge.
Hints are continuously communicated through the chatbot, and a pop-up is automatically triggered when no progress is made after a certain amount of time. Hints become more apparent and clear the longer there is inactivity, allowing players to figure out challenges with varying degrees of assistance. If players really get stuck, they can switch to work on another hacker’s different challenge or wait longer for a more guided hint.
Cloud security incidents happen every day. In almost every case, security vulnerabilities can be attributed to the cloud subscribers’ poor security practices, not any given cloud service provider’s negligence. We hope Forescient, Security Innovation’s newest cloud cyber range can help you reduce the risk of a cloud security incident or mitigate its consequences.
Forescient is now part of our limited-edition Cloud Security Readiness Package. Check it out how you can see it in action.



