When it comes to personal security best practices, there are some pieces of advice that are universally good ideas:
- Use a password manager to create strong unique passwords
- Lock and encrypt all your computers and mobile devices
- Use 2-Factor Authentication on your important online accounts (email, banking, social media)
- Keep your devices up-to-date with the latest security patches
- Be cautious of what networks you connect to (free WiFi comes at a cost)
This is pretty good advice for everyone, and if you are not already doing most of the above, this list is a good place to start when trying to improve your personal security. Beyond that, however, each of us interact with the connected world in different ways. As a result of this, the risks and threats we face can vary drastically. If I were to give you advice on how to be ‘super safe’ on the Internet, I would probably overwhelm you with a number of technical processes and technologies that would seem like a monstrous challenge to implement. You would also find that implementing those recomendations would also drastically change your experience and the ease with which you currently interact with technology.
“But… If being ‘super safe’ is so much work, how do you do it?”
Thanks for asking. I believe that for the typical user, small adjustments in behavior can drastically improve their personal security and safety. What we can do is determine where you are at the most risk, then implement small precautions that can be taken to reduce that risk.
“Yes, but how?”
Well, for that you need a “Personal Threat Model”. Your personal threat model is something you develop and refine over time to evaluate the risks associated with protecting your most valuable assets. In the coming weeks, I will be sharing the full details of how to create your own personal threat model at the upcoming Atlantic Security Conference. After the talk, check back here for the full video. Until then, let me share the basics.
Creating your Own Personal Threat Model
To create your own personal threat model, ask yourself the following questions, take some notes, and think about it a bit:
- What are the assets you care most about protecting? (emails, images, video, your location, identity, financial information, etc.)
- Who are the different user groups you interact with? (friends, family, employer, random person on the train)
- What are the systems where your data is stored? (Websites you frequent, devices, and services)
- How do all of these things interact? (It usually helps to draw a picture)
- What are the rules I want to maintain? (Who can see my pictures? How much can my employer know about me?)
- What are the top threats that I am worried about?
- What steps can I take to best protect against the top threats?
I went through this process in detail and ended up with the following diagram that describes the way I interact with the world. By no means do you have to be as detailed, but if it helps you get an idea for what your threats may be, feel free to use it as a template.
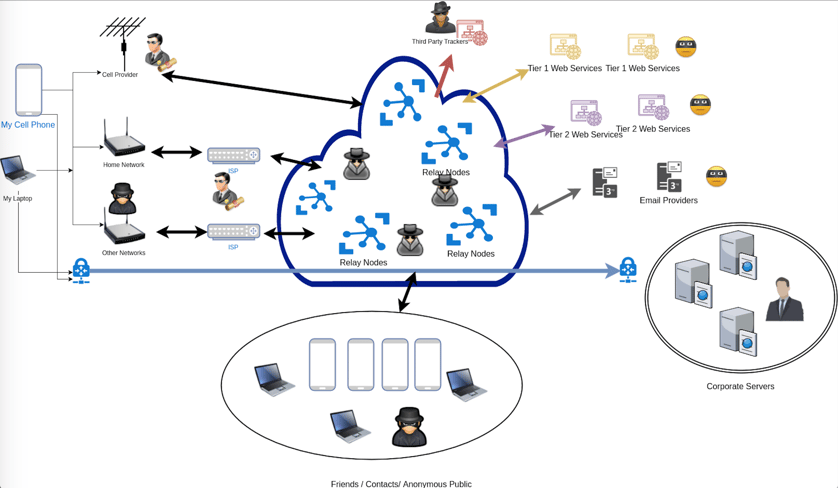
With this diagram and answering all the above questions, I came up with the following top 7 threats that I am most concerned about:
- Unauthorized read of sensitive personal media
- Unauthorized creation, read, update, or delete of financial information
- Unauthorized read, update, or delete of business assets
- Unauthorized read of authentication credentials
- Unauthorized read of personal communications
- Unauthorized read of sensitive information not disclosed publicly (all other groups)
- Foreign government can read authentication credentials or business assets
For me, protecting business, financial, and personal assets are very important, so this is where I will focus my energy. When it comes to defense, I do the following things (amongst many others):
- Use a password manager to protect and manage authentication credentials
- Take great care about not storing business assets insecurely
- Take burner devices when I cross a national border
- Use the Signal app to communicate with close friends, my lawyer, and other contacts
- Frequently review financial statements and carefully track where I supply financial information online
You might not need to take the same precautions as me when it comes to protecting business assets or sensitive conversations, and that’s ok. You may notice that nothing in my top 7 list mentions things like anonymity or worrying about people knowing my location. Although this is a concern, it is not among my top concerns. For some people, say hiding from a stalker or abusive partner, this list might look drastically different.
The point that I want you to take away from this post is that you don’t have to stress about doing everything perfectly, just start making small changes where you can have the most impact on your security posture and personal safety. For a full walkthrough on how to build your own personal threat model, be sure to check out my full talk at AtlSecCon or check back to this post once the video has been posted.
If you have any questions please feel free to reach out to me directly on twitter @mrvaughan. If you came to this post because you are looking for security advice because you are greatly concerned for your safety, please don’t hesitate to reach out directly, and I will do my best to connect you with additional resources.


