Over the past 18 months, a small group of us at Security Innovation have been delving into hacking at the physical layer. This layer covers the physical movement of 1s and 0s over cables or through the air, such as through an Ethernet cable or over a wireless signal. Penetration testing rarely touches the physical layer, and while it may be under-discussed in most circles, we also know that it can be quite fruitful.
Part 1: Picking a Target
It’s easy to think about common systems like Bluetooth and WiFi as if the data is simply moving from A to B over the air. This seems especially true with handheld things like TV remote controls, car key fobs, or garage door openers that somehow seem more focused and directional. But this isn’t true. The signals for these devices usually spread nearly omnidirectionally, radiated from the antenna.
Anyone in range of the signal can mess with it, and that’s exactly what we wanted to do. We were very interested in devices that used their own custom radio protocols. It’s in this space that we encounter power and water meters, remote controls, display signs, electronic keys, drones, thermostats and sensors, and many more. Devices in this space fly under the radar of the usual network attacks, but as software-defined radios become inexpensive and trivially accessible, the remote controls and keys are still trusted.
There are many fascinating attacks at this layer too. For example, in this video, someone signals a gas pump into a standalone and calibration mode, a mode that allows the pump to run without the use of the payment system, which the thief then uses to steal $400 in gas. Samy Kamkar has a public tool called OpenSesame that efficiently brute-forces the access codes in remote garage door openers, opening some models within seven or eight seconds. The more recent Rolling Pwn exploit abuses the codes sent from several brands of car key fobs, allowing an attacker to unlock the car remotely. It is things like this that caught out attention.
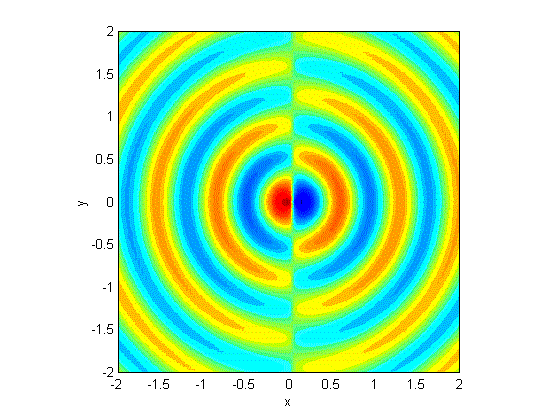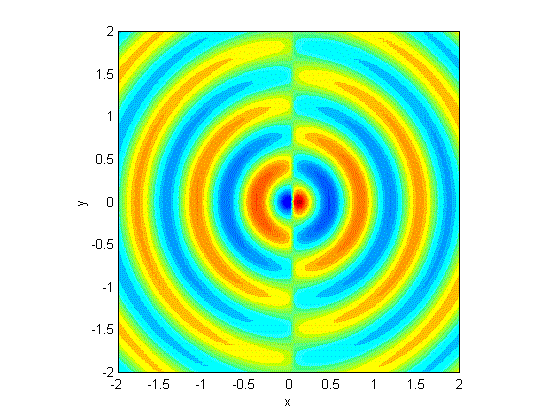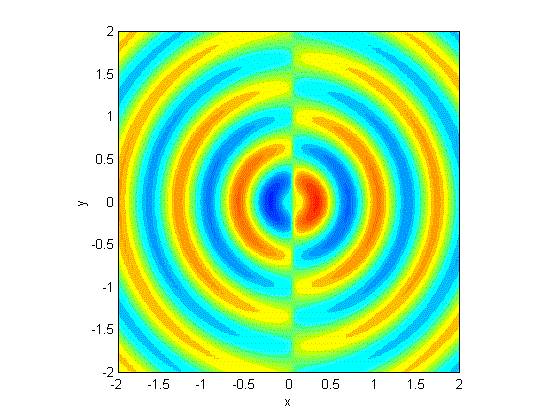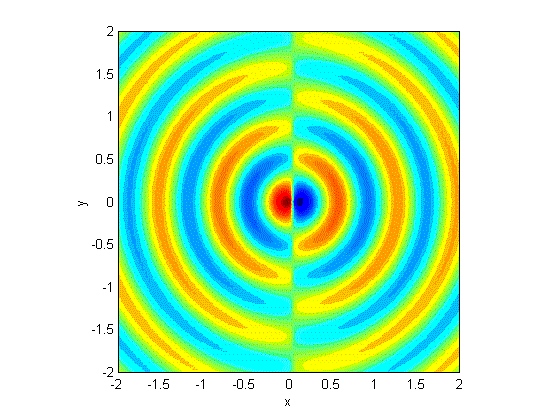
We were particularly interested in devices that used frequency-shift keying (FSK), a technique of modulating a radio wave to carry digital data by changing the frequency back and forth very quickly. FSK is very popular in inexpensive devices that deliver a simple command, like a remote control; or a small amount of data, such as from a sensor. It is also easy to recognize in RF hacking tools. The signal ends up looking something like this:
 Frequency-shift keying, where the waves are digitally transformed between an upper and lower frequency for the 1 or 0.
Frequency-shift keying, where the waves are digitally transformed between an upper and lower frequency for the 1 or 0.
 Key fobs typically use FSK as well. These are my keys, and they have a specific vulnerability that we will cover soon.
Key fobs typically use FSK as well. These are my keys, and they have a specific vulnerability that we will cover soon.
It started in mid-2021. The two of us, Maxwell Dulin and Jesse Victors, began exploring different types of modulation that embed digital data within radio waves. Some modulation methods, such as frequency-hopping spread spectrum, can get quite complex, making it extremely challenging for an outsider to decode and explore. However, simpler methods of modulation are quite common in everyday hardware devices, such as on-off keying or frequency-shift keying. Our first targets were our own garage doors, discovering one brand with a wireless vulnerability and an undocumented bug in the receiver. Next, we looked at a cheap set of LED lights with a remote control that operated at a much higher bit rate. And we continued looking for devices that had not been examined before.
The answer came to use several weeks later. One day, Maxwell was watching a basketball game when the thought occurred:
Could a hacker influence the result of a game by hacking the scoreboard?
It’s not out of the question. Most scoreboards, particularly at amateur games, are controlled wirelessly. The scoreboard is considered a trustworthy source for the score, game time, and other game states. To our surprise, we have not been able to find any other online examples of anyone attacking a game scoreboard. We immediately set our eyes on this target and got to work immediately.
 Our first goal was to pick a specific scoreboard. There are many, many different models out there, but scoreboards are relatively simple, and they all do about the same thing. We assembled a list of about 120 potential models and slowly whittled it down. Soon we were left with a short list of scoreboards that only used frequency-shift keying, and we picked one for this research project.
Our first goal was to pick a specific scoreboard. There are many, many different models out there, but scoreboards are relatively simple, and they all do about the same thing. We assembled a list of about 120 potential models and slowly whittled it down. Soon we were left with a short list of scoreboards that only used frequency-shift keying, and we picked one for this research project.
Our objectives were to perform purely radio-level attacks. Realistic attackers wouldn’t have physical access to either the scoreboard or the display, but, in our mind, they could mess with the scoreboard if they were in the area. Maybe they put their hardware in a backpack. Maybe they could put it in a nearby tree.
Our scoreboard arrived at the Seattle office within a week. The Score9 (the real name withheld) scoreboard comes in several modular components, and we ordered the transmitter and the receiver. The receiver connects via HDMI to a monitor or a larger game display, so we had everything that we needed for wireless attacks. Over the next six weeks, we discovered (and disclosed to the vendor) several serious and stealthy vulnerabilities. We believe that this is the first time that a scoreboard has been hacked.
Getting there was a journey. A journey into reverse engineering, radio demodulation, hardware attacks, and a bit of math.
To read Part 2 of this attack, click here.
Timeline:
- 05/06/2021: Started researching RF attacks against scoreboards
- 11/01/2021: Score9 scoreboard selected
- 11/09/2021: Research project initiated
- 12/01/2021: Score9 scoreboard arrives at the office
- 02/23/2022: Discoveries presented internally
- 06/20/2022: Disclosure vulnerability policy updated
- 07/29/2022: Vendor alerted to vulnerabilities, no response
- 08/15/2022: Follow up with vendor, no response
- 09/12/2022: Part 1 published
About Jesse Victors, Senior Security Engineer
Jesse Victors is a senior security engineer at Security Innovation. His technical interests include privacy and anonymity systems, password cracking, RF attacks, and applied cryptography. Jesse has also published The Onion Name System: Tor-powered Decentralized DNS for Tor Onion Services and spoken at the Privacy-Enhancing Technology Symposium. In the evening you can often find him in virtual reality games, fiddling with amateur radio antennas, and networking with orbiting satellites. Jesse has pursued information security since 2014. Connect with him on LinkedIn.
About Maxwell Dulin, Senior Security Engineer
Maxwell Dulin is a senior security engineer at Security Innovation who specializes in web application security and IoT security. He has also spoken at DEFCON for his IoT research on the Zyxel NAS and is the founder/creator of the Spokane Cyber Cup. In his free time, he plays dodgeball and enjoys hiking. Connect with him on LinkedIn.


