For those trying to keep their identity secret, Tor is arguably the most powerful tool available. Its use of onion routing with one of the industry’s largest networks makes it difficult for an adversary to deanonymize users. However, this anonymity comes at a cost to latency and bandwidth.
In a world where data is increasingly bought and sold, many internet users are looking to conceal their browsing habits from their ISPs and web trackers. For these relatively small or disinterested adversaries, Tor is overkill. An alternative for these users is a VPN, but they have their own set of drawbacks. In particular, most VPNs are either paid or ad-supported.
For my intern research project, I set out to bridge the gap between Tor and VPNs by creating a versatile tool that compromises between anonymity and speed.
The Basics
The project, dubbed Torantula, started as a more general implementation of Tor Button's domain isolation, which sends traffic to different domains through different Tor circuits. What I wanted to do was implement something similar that could be put transparently in front of any SOCKS-capable application, even if they do not support isolating Tor streams themselves.
In essence, Torantula isolates Tor streams in a more lenient way than the Tor client can by default. This, coupled with the ability to reuse streams, reduces the latency when connecting to new addresses.
The Unethical Bit
With Torantula successfully acting as an intermediate proxy and able to control the circuits that streams go through, a thought entered my head: what if I added the ability to also send streams over different Tor processes.
Intuitively, I didn't think this would do much. However, I knew Tor throttled clients at guard nodes to keep the network less saturated, so I figured it was worth a shot to see if I could get better bandwidth by using multiple processes.
The results were better than I expected.
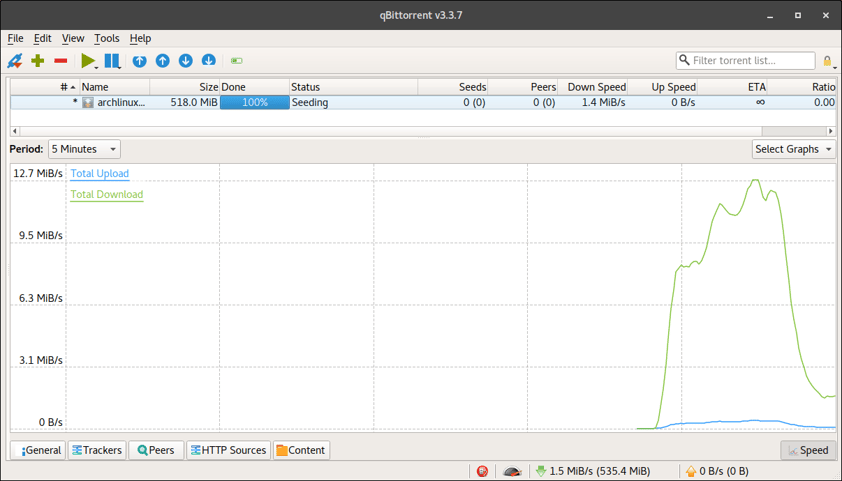
Yes, that's 12.7 MiB/s, about 100 Mb/s, through Tor. Granted, this type of speed can only be realized when it is one client talking to several independent clients. This limits the use-cases where such bandwidth can be achieved to things like torrenting, large-scale port scanning, and web crawling. Still though, that's almost 100 Mb/s through Tor.
That said, I'd be remiss to not mention the downside of this. For one, torrenting over Tor is notoriously prone to leaking information about the user. Further, you're abusing the network pretty badly. That bandwidth you're using to download Arch Linux could ethically be better utilized by a political dissident or whistleblower.
Risks
I set out to fine-tune Tor for speed and there were definitely some improvements in that realm. However, in all cases where Torantula yields better performance, it is at the cost of a more relaxed security measure. If you absolutely need security and anonymity, stick to using Tor directly or through Tor Browser. Torantula is for those with little to hide, who are facing weak adversaries, and want some more speed.
Torantula is available for download and use at https://github.com/SecurityInnovation/Torantula. I was only able to test it on Linux, but it'll probably work fine on OS X, too (Maybe with minor tweaking).
For a more technical overview of Torantula, visit http://garrettmarconet.blogspot.com/2017/09/tuning-tor-for-performance.html
Written by Garrett Marconet, Security Innovation Intern


