As Attack in Autumn 2020 wraps up, the Security Innovation team would like to thank everyone who has helped build a community of Cyber Rangers. Since our first Hack Through the Holidays event in 2018, we’ve seen participants of all backgrounds and skill levels expand their talents with our CMD+CTRL Cyber Ranges. To help even more people learn, we’re forgoing the same old event recap blog and sharing something a bit more interesting. We hope you enjoy it!
Over the last two years, the Security Innovation team has profiled a variety of new and experienced members of our community. Whether they were High School students or seasoned security professionals, one thing remained the same: they all had curious minds with a thirst to learn more!
One of our first profiles was Brandon Evans. At the time, Brandon was a Software Engineer who has since shifted his professional focus to software security. Needless to say, we’re excited to have been a small part of that journey for Brandon. We also want to share a really interesting piece of work that Brandon and his co-workers did with our team to identify and fix a 0-day issue in our InstaFriends site.
Before we jump into the details, there are a few important points for our community of ethical learners to remember:
- No user data, customer data, or systems were put at risk. That’s the beauty of cloud-based Cyber Ranges – you can grow important security skills without risk to your organization!
- Brandon was outstanding about responsibly disclosing the details of this 0-day so our team could protect our intellectual property. We urge all others to do the same.
pFinally, our team is sharing these details for one really important reason: securing systems is hard! Securing those systems is even more difficult when vulnerabilities are intentionally included! Security Innovation is committed to educating security practitioners and testing systems to help improve their posture. At the same time, security is also a never-ending journey where even the most security-minded developers and testers miss incredibly rare edge cases. If a 0-day can exist in one of our well-designed and tested systems, then it can exist anywhere.
With these important points in mind, please enjoy Brandon’s write up.
Cyber Ranges: A Balancing Act
Security Innovation has a wide array of high-quality cyber ranges that help the community learn more about ethical hacking and common web application flaws. I made the decision to go into application security full-time in-part because of how much fun I had taking on their Shadow Bank and Gold Standard ranges at AppSec California 2019. Since then, I have participated in every online CMD+CTRL event until I completed their entire suite, and I loved every minute of it.
Developing a Cyber Range is a balancing act. By definition, the range needs to contain a myriad of security vulnerabilities that would be devastating to a real organization. Thankfully, because these sites do not have real customers or any of their data, most of these vulnerabilities are harmless if contained to the range. However, a small minority of these vulnerabilities can actually affect the company providing the range. Examples of these critical vulnerabilities include ones that allow for a denial of service, resource hijacking, or intellectual property theft.
Understanding this, the CMD+CTRL team has taken several precautions to contain the damage performed in their ranges. One key protection that they have implemented across multiple ranges is a mechanism that blocks arbitrary code execution. Even though many of these ranges have Unrestricted File Upload vulnerabilities, their platform detects when a file with a dangerous filetype is loaded and blocks it from executing.
Though the team has an overall great track record of preventing catastrophic exploits, even the most skilled developers can miss extreme edge cases! It is impossible to predict all of the ways participants will chain known issues together to craft an exploit. Below is a detailed write up of a 0-day I found in InstaFriends with two of my co-workers, Jessica Wood and Kirill Kulakov. We worked with Security Innovation to demonstrate and help patch the vulnerability.
Anatomy of InstaFriends Photos
To understand the issue, you first need to understand one core component of InstaFriends: the ability to share photos. When a user uploads a photo, InstaFriends renames the file and stores it on the underlying virtual machine. Users can then request to see a photo, and if they are authorized, the application will load the file from the filesystem and serve it to the requesting user. After analyzing the database schema, which we were able to do by exploiting an intentional SQL Injection vulnerability using sqlmap, we determined that the database mapped users to their photo files using a table called UserPhoto.
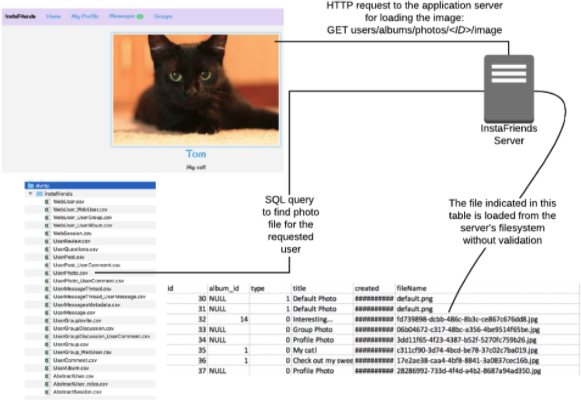
A workflow diagram detailing how images are loaded on InstaFriends.
With this discovery, we wondered if this functionality could result in a Local File Inclusion vulnerability. What would happen if a user had their fileName column set to ../../../etc/passwd? Would the application load that file on the server’s filesystem and serve it to the requesting user?
To determine this, we would need to be able to control the fileName column. We fiddled with the photo upload system for hours to see if we could prevent it from renaming the uploaded file. If we were successful, we could theoretically overwrite files on the filesystem as well. Unfortunately, we couldn’t crack this feature due to the strong security controls implemented by the Security Innovation team.
Crafting an Exploit
The next day, we had an epiphany: why exploit the photo upload system? We already knew of several SQL injection vulnerabilities in the application. Couldn’t we just modify the contents of this table using such an injection? The answer: absolutely!
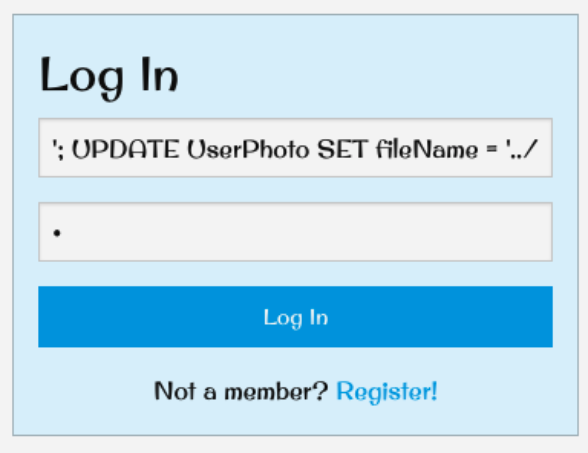
Exploiting a SQL injection vulnerability in InstaFriend’s Log In form to modify the file name associated with every user. '; UPDATE UserPhoto SET fileName = '../../../etc/passwd' --
Once this injection string was executed, the most noticeable result was that every image on the website would break. This is only because the browser cannot render a text file as an image. After downloading one of these “broken images” and opening it in a text editor, we saw the contents of the /etc/passwd file! This file has limited value because, even if it used the legacy format containing the password hashes of the server’s users, which it did not, the server’s SSH port was not accessible from the public internet.
Next, we asked if any of the other files on this server could be of use. Not knowing the answer, we created a script that automates the process of modifying the database and downloading the specified file using a list of well-known Linux files. It turns out that the file /proc/self/cmdline contains the command used to spawn the process that is reading the file. Because the InstaFriends application is reading the file we requested from the filesystem, downloading this file will indicate the command used to launch InstaFriends. That command contained the path to the executable file: /usr/local/instafriends/instafriends.jar
Repeating this exploit for this file, we were able to download the InstaFriends executable JAR file. This alone would allow us (technically, not legally) to run the application on our own servers.
The Aftermath
The specifics of this vulnerability are a lot of fun, but the issue has been fixed for over a year. I hope this writeup will inspire you to push the boundaries of these Cyber Ranges even further, so long as doing so does not break the rules of engagement. Most importantly, if you find an issue of this magnitude, make sure to contact the CMD+CTRL team. They are able to run free cyber ranges on a regular basis thanks to the cooperation of participants who agree not to perform public writeups of the challenges. So, keep on hacking, but always do so ethically!
To learn more about me and my introduction to the world of application security, check out my past interview with Security Innovation, Give Hacking a Try…You Might Just Be Great!
![]()
The awesome 8-Bit avatar the Security Innovation team created for me after an event.


